It is the most popular web browser on the planet and is installed on over 3.5 billion computers.
But Google Chrome users have now been warned to update their browser immediately to avoid being targeted by hackers.
In a security bulletin, Google says it has now patched a high-severity issue which allowed criminals to infiltrate target computers.
And the tech giant says that criminals, even possibly nation states, have already exploited it.
The issue was found in a system called Chrome V8, which allows the browser to run code found on websites efficiently.
However, the flaw allowed hackers to create malicious webpages which could steal visitors’ data, passwords, or even deploy viruses and ransomware.
Google says it has now fixed the vulnerability, but you will need to ensure your browser is updated to the latest version to be protected.
Jake Moore, global cybersecurity advisor at ESET, told MailOnline: ‘Updating your devices and apps is vital and browsers are no different and just as essential to fix security holes like this one.’

Chrome users have been warned to update their browser as soon as possible, as cybersecurity researchers discover a high-severity issue that has already been exploited
This bug allowed hackers to execute so-called ‘read/write’ operations, allowing them direct access to information on the browser.
Mr Moore says: ‘Criminal hackers could have been able to take advantage of this vulnerability to read anything stored in the browser’s memory, which, worryingly, could include sensitive information like passwords.
‘If a threat actor were to get into an account with such credentials, they could then target other people in the victim’s contacts with relative ease.’
Google’s security bulletin gave the vulnerability, dubbed CVE-2025-6554, a severity score of 8.1 out of 10 – ranking it as a ‘high’ threat issue.
The flaw is particularly attractive to criminals because it is a ‘zero day’ exploit, meaning that the flaw wasn’t even known to Chrome’s developers.
These are risky because criminals can often start using zero-day exploits to launch attacks before a security patch is prepared.
In this case, Google has confirmed that hackers have already been exploiting the vulnerability to launch attacks.
The bulletin says: ‘Google is aware that an exploit for CVE-2025-6554 exists in the wild.

The flaw allows criminals to insert malicious code onto your device or extract critical information such as passwords (stock image)
Google says it won’t be releasing any more information until ‘a majority of users are updated with a fix.’
However, based on the team that spotted the issue, the attacks may have been made by very powerful groups.
The vulnerability was spotted by Clément Lecigne of Google’s Threat Analysis Group (TAG).
This cybersecurity organisation is usually responsible for tracking threats posed by nation-states and so-called advanced persistent threats (APTs).
Given that the flaw has already been exploited, it seems likely that it may have been used by nation states in highly targeted attacks.
Previous flaws in Chrome V8 have been used in the past to hack journalists, political dissidents, IT admins and other key targets for interference.
Mr Moore says: ‘A flaw this serious could be used by anyone with the determination and the right knowledge to take advantage of it, which could easily include nation state actors.
‘Such groups often look for extremely powerful vulnerabilities to spy on highly targeted people, such as government employees, like with the infamous Pegasus spyware.’
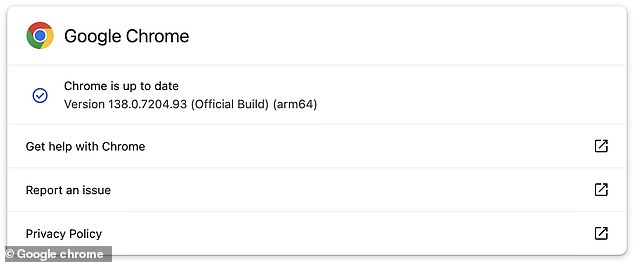
Google has already patched the issue, so ensure that you are updated to the latest software version to get protected
Google Chrome is usually updated automatically, installing all the latest security patches.
However, if you want to ensure you are protected, you can also manually check your software version and update the browser.
First, open the browser and select the drop-down menu in the top-right-hand corner.
From there, click on Help, and select ‘About Google Chrome’.
This will show your current software version, which should be updated to 138.0.7204.96/.97 for Windows, 138.0.7204.92/.93 for macOS, and 138.0.7204.96 for Linux.
If you are not on the latest version of the software, select ‘Relaunch’ to restart Chrome and install the update.
If the ‘Relaunch’ button is not visible, this means you are already on the most up-to-date version.
Google has been contacted for comment.
